Rachit Arora
gRPC Pentesting
Feb 17, 2024I was doing PC box from Hackthebox when I came learnt about gRPC, which made me curious and I delved deeper.
This article is a compilation of various resources I’ve studied, and I’ve provided links below if you’d like to delve deeper into the topic.
What is RPC?
In distributed systems, we often have to communicate between different services. Code that may look like a local function call, is actually being executed on a different node in another system entirely. This is known as a remote procedure call or RPC.
What is gRPC?
gRPC is a modern open-source high performance Remote Procedure Call (RPC) framework. It has been designed to run in any environment. It can efficiently connect services in and across data centers with support for: Load balancing, tracing, health checking, authentication.
If you wanna dive deep into how exactly gRPC works, this is awesome.
Getting to Know gRPC HackerNoon
gRPC is built on top of HTTP/2 so it’s ideal for bidirectional communication; the client can initiate a long-lived connection with the server, over which RPC calls can continuously be sent.
HTTP/2 allows server-push, where with 1 single request from client, server can send back multiple responses. This is extremely valuable to reduce the round-trip latency between client and server in many cases, when server knows exactly what resources client will need and send them before they’re even requested.
For more deeper information about how exactly gRPC works, use the article down below
Identifying gRPC-Web traffic
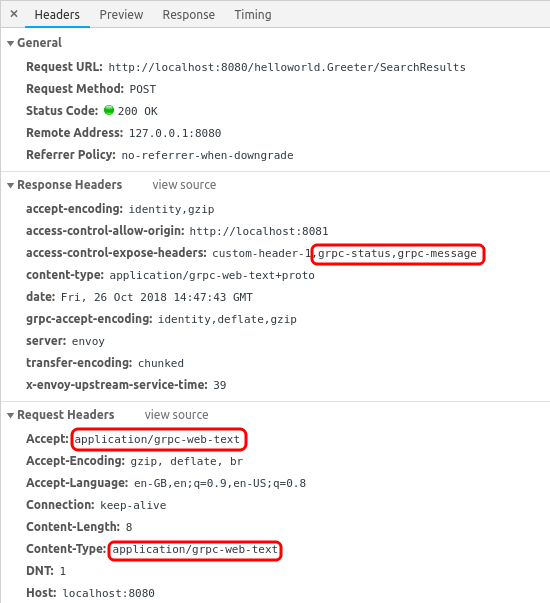
Looking at the HTTP headers of intercepted traffic, we see tell-tale “grpc” in several locations such as
- Accept request header
- Content-Type request header
- Access-control-expose-headers in the response header
Note the “grpc-web-text” application type. For the remainder of this article we assume that this is being used, however it is worth nothing that this is not the only possible value [Ref1].
Theres a way to reverse engineer gRPC, I would really recommend reading the article down below
Pentesting Twirp/gRPC-Web : Recon and Reverse-engineering
Tools to interact with gRPC
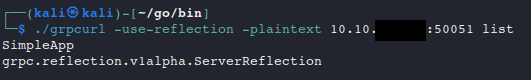
- grpcurl found on GitHub
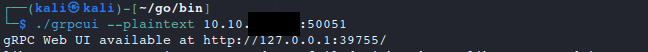
- grpcui found on GitHub
If you use the bind parameter to bind it to some IP address that differs from loopback(127.0.0.1) then your browser will gladly proxy your connections to Burp or ZAP. After that you can continue your “regular pentesting workflow” .
- Postman
- Insomnia
For deeper knowledge about the Tools you can use, refer to the article below
Vulnerabilities in gRPC
A very cool blog about the ways you can go about “Pentesting” gRPC, I do not have the same infra to test these on, but I can definitely link you that
Another article by the same authors
Have any questions
Do you have any questions? Feel free to reach out to me on twitter or on LinkedIn.