Rachit Arora
Finding and reporting CVEs & what it actually teaches you
Apr 20, 2024Contents
- Why it is more than just a CVE?
- CVE Application Process
- How do you look for CVEs?
- Leveraging your work
- Lessons Learnt
Discovering and disclosing CVEs involves more than just having your name associated with a vulnerability.
Why it is more than just a CVE
I personally found 2 CVEs as of now,
CVE-2023-47184
- Auth. (admin+) Stored Cross-Site Scripting (XSS) vulnerability in Proper Fraction LLC. Admin Bar & Dashboard Access Control plugin <= 1.2.8 versions. More information about CVE-2023-47184 here
CVE-2023-49743
- Auth. (admin+) Stored Cross-Site Scripting (XSS) vulnerability in Dashboard Widgets Suite <= 3.4.1 versions. More information about CVE-2023-49743 here
CVE stands for Common Vulnerabilities and Exposures. Managed by MITRE, the CVE database serves as a collection of publicly disclosed vulnerabilities. When MITRE publicly discloses a CVE, it represents the initial disclosure of a previously unknown vulnerability, often referred to as a Zero Day vulnerability discovery.
Many people find the process of acquiring CVEs daunting. However, whenever you mention having a CVE to someone, it grabs their attention. They become curious about what you discovered.
It doesn’t matter if it’s a simple finding like a cross-site scripting vulnerability or a sophisticated attack targeting Microsoft systems. What matters is that you’ve conducted thorough research and identified something noteworthy, something that hasn’t been reported before. Being able to distinguish yourself in this way is significant.
I was on chat with a professional for an advice, and while looking through my profile he mocked my XSS CVE, atleast i went out of my way and found something and reported it to officials.
Finding a CVE that is reported to MITRE shows a person’s initiative, ability to research, create proofs of concept, write technically, and manage client communications
How do you look for CVEs
WordPress is a free and famous open source CMS(Content management system), which is used to create flexible websites thus used by approximately 75 million websites.
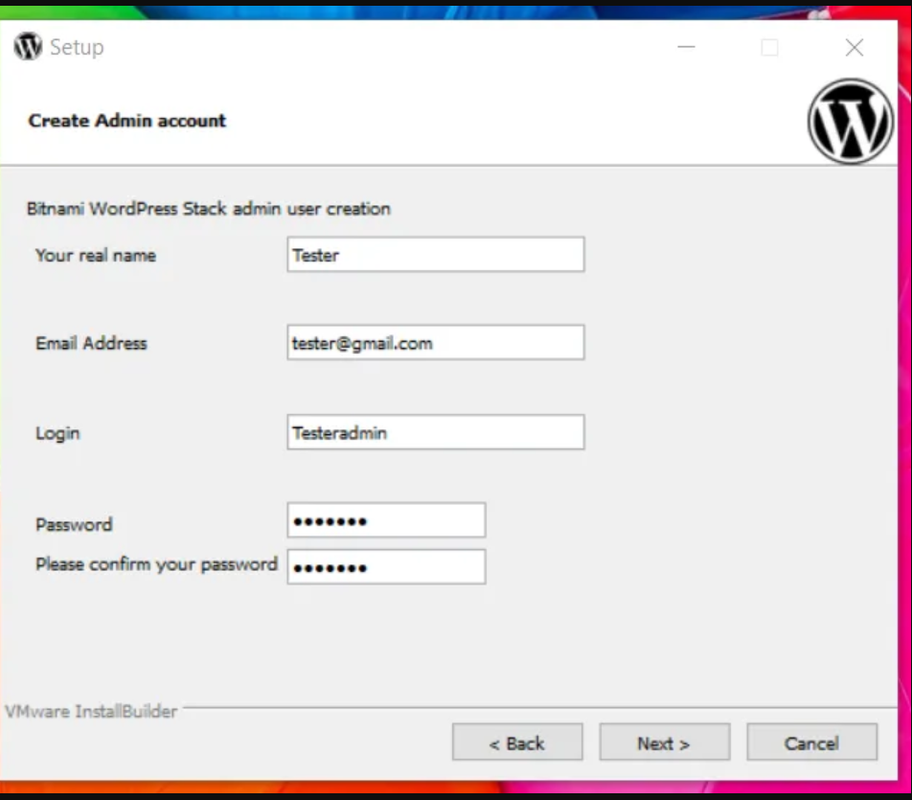
We can download and install wordpress locally
https://bitnami.com/stack/wordpress/installer
Open Mozilla Firefox browser and type localhost/127.0.0.1 and hit enter. Page as shown below will appear, you need to click on Access WordPress.
Open the WordPress admin page just append wp-admin/admin after the URL and login
http://localhost/wordpress/wp-admin
After logging into the WordPress admin dashboard, go to Plugin » Add New, and enter the plugin name in the search field to install it. Once installed, activate the plugin by clicking on Activate Plugin. With the plugin installed and activated, you can start testing with basic XSS.
CVE Application Process
The process for applying for a CVE can feel daunting, especially due to the lack of references on the process. Here’s how it typically works:
- Determining Developer Status:
- The initial step involves determining if the developer is a “Certified Numbering Authority” (CNA).
- Developer Status as CNA:
- If the developer is a CNA, the CVE application process must be handled through the developer.
- Developer Not a CNA:
- If the developer is not a CNA, the application process is managed by MITRE.
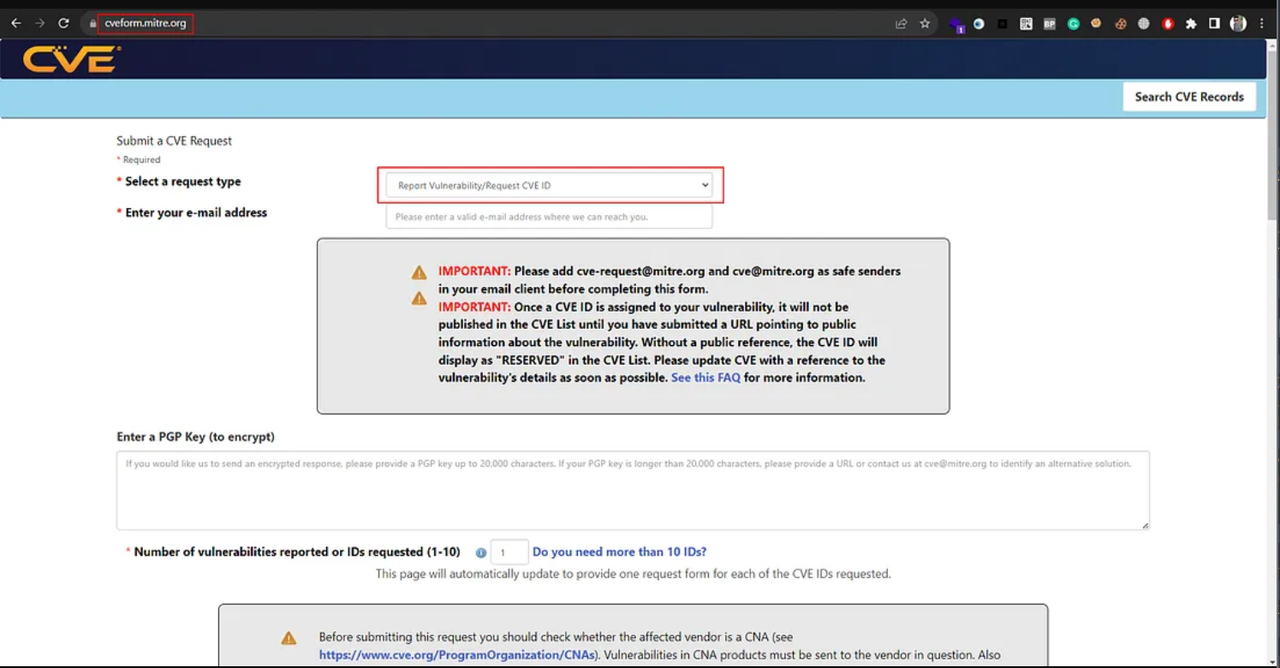
To obtain the CVE-ID, the first step is to raise the request in https://cveform.mitre.org/
Reporting the Vulnerability: Using the CVE Form: Imagine the product you’ve found a vulnerability in isn’t listed. No worries, just head over to https://cveform.mitre.org/. Opt for “Report Vulnerability/Request CVE ID” and fill in vital information — vulnerability type, vendor, product, version, attack type, impact, and description. Then, wait for the next steps to unfold..
Earning Your Temporary CVE Number: In around 15–20 days, if your discovery aligns with the criteria, you’ll receive a temporary CVE number — a validation of your findings and their significance.
Sharing Your Publication: Sharing Insights: To bring your CVE ID to life, translate your findings into a well-structured write-up. Platforms like Medium, GitHub, or Exploit-DB are excellent choices. Your write-up isn’t just documentation; it’s an avenue for sharing knowledge and raising awareness.
To publish your exploit, you are to send a mail to the exploit DB team. The team will review the exploit and will publish it.
Make use of template to send the exploit details.
Email id: **submit@offsec.com**
# Google Dork:
# Date:
# Exploit Author:
# Vendor Homepage:
# Software Link:
# Version:
# Tested on Windows
# Patched Version:
# Category: Web Application
# CVE:XXX
# Exploit link:
Notifying CVE About Your Publication: Final Step: Back to https://cveform.mitre.org/, but this time, select “Notify CVE About a Publication.” Share the link to your write-up. The CVE team verifies the publication and updates their database, cementing your contribution.
The Final Countdown: Your CVE Goes Live: Now, here’s the exciting part: The CVE team will acknowledge receipt of the information. In a few short hours, your CVE will go live, contributing to the collective digital security effort.
NIST will also assess the findings and update resources with a CVSS score
CVE Numbering Authorities (CNAs)
CNAs are vendor, researcher, open source, CERT, hosted service, bug bounty provider, and consortium organizations authorized by the CVE Program to assign CVE IDs to vulnerabilities and publish CVE Records within their own specific scopes of coverage.
They are Authorized to assign CVE IDs to vulnerabilities affecting products within a distinct, agreed-upon scope.
Leveraging your work
Update your LinkedIn biography and resume with those two, or a blog if you have one.
Lessons Learnt
As I mentioned, obtaining a CVE involves more than just acquiring a name and a number. The entire process proves you’ve conducted thorough research and identified something noteworthy, something that hasn’t been reported before.
Discovering a CVE and reporting it to MITRE demonstrates an individual’s initiative, research capabilities, proficiency in creating proofs of concept, technical writing skills, and ability to manage client communications.